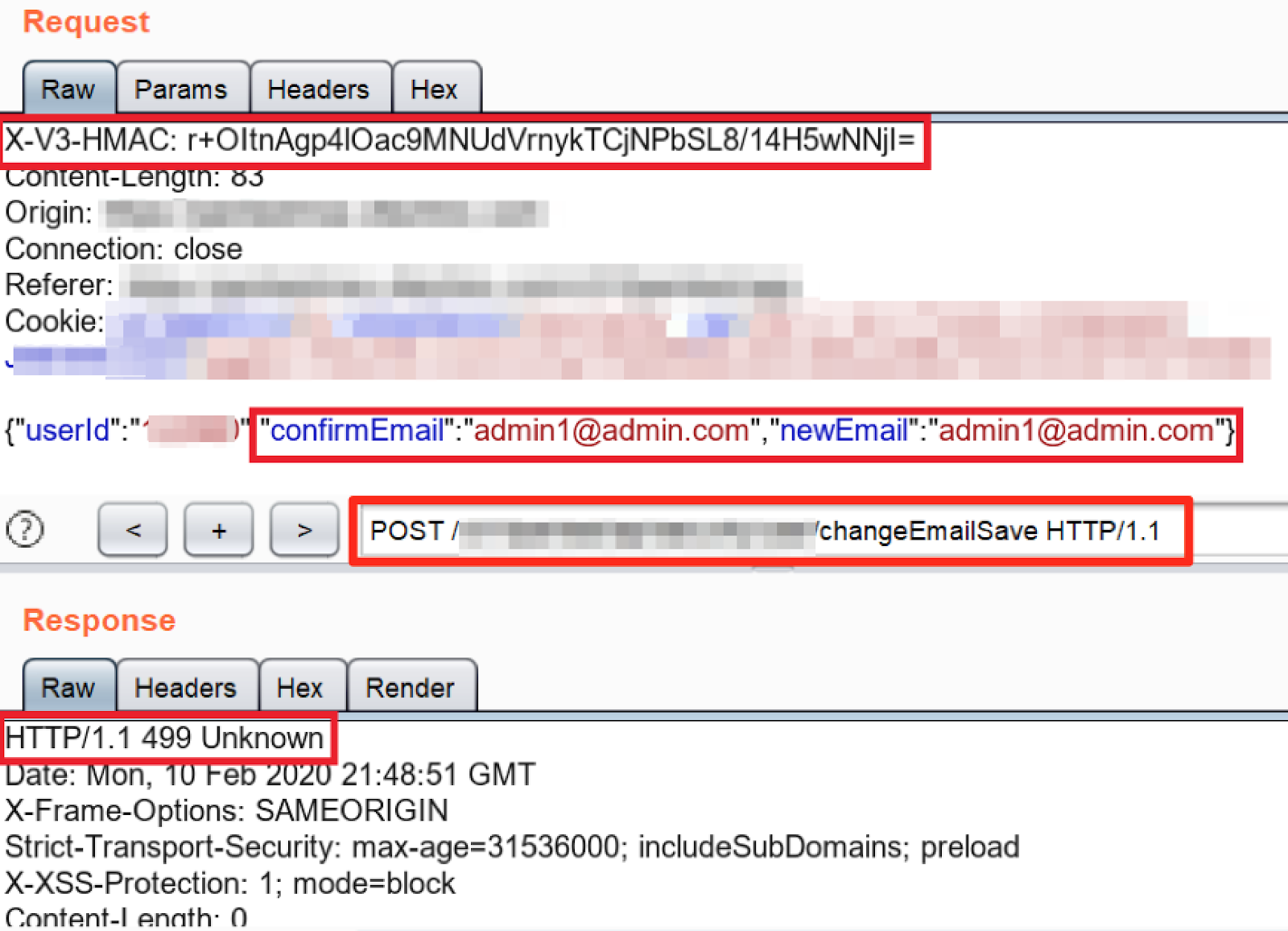
Automating Pentests for Applications with Integrity Checks using Burp Suite Custom Extension | NotSoSecure

Hands-On Application Penetration Testing with Burp Suite: Use Burp Suite and its features to inspect, detect, and exploit security vulnerabilities in your web applications: Lozano, Carlos A., Shah, Dhruv, Ahemed Walikar, Riyaz:

How to Secure API Endpoints in iOS and Android Apps Using Burp Suite Community Edition: A Step-by-Step Guide to Pen Testing and VA