
Penetration Testing Tutorial | Penetration Testing Tools | Cyber Security Training | Edureka - YouTube
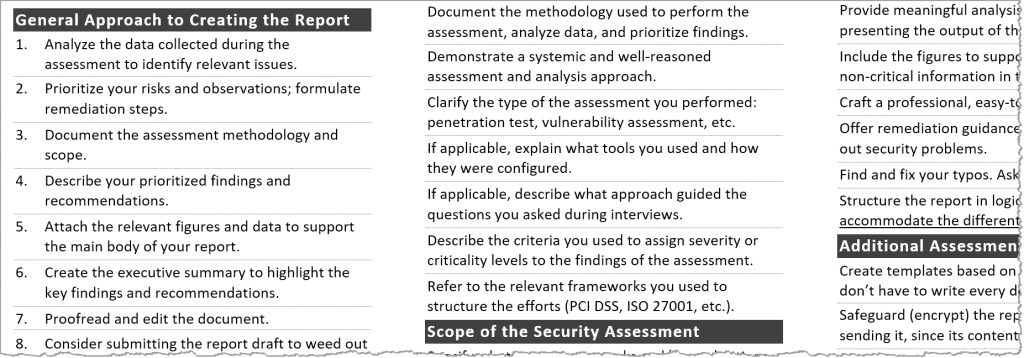
SANS Penetration Testing | Tips for Creating a Strong Cybersecurity Assessment Report | SANS Institute

Computer Hacking Beginners Guide: How to Hack Wireless Network, Basic Security and Penetration Testing, Kali Linux, Your First Hack: T. Norman, Alan: 9781980390978: Amazon.com: Books

SOLUTION: Hacking beginner to expert guide to computer hacking basic security and penetration testing computer science series pdfdrive - Studypool


![PDF] Computer Security and Penetration Testing by Alfred Basta eBook | Perlego PDF] Computer Security and Penetration Testing by Alfred Basta eBook | Perlego](https://www.perlego.com/books/RM_Books/cengage_umaorujg/9781285964027.jpg)
![An Introduction to Cyber Security: A Beginner's Guide [Updated 2023] An Introduction to Cyber Security: A Beginner's Guide [Updated 2023]](https://www.simplilearn.com/ice9/ebooks/frs_banner_cs.jpg)



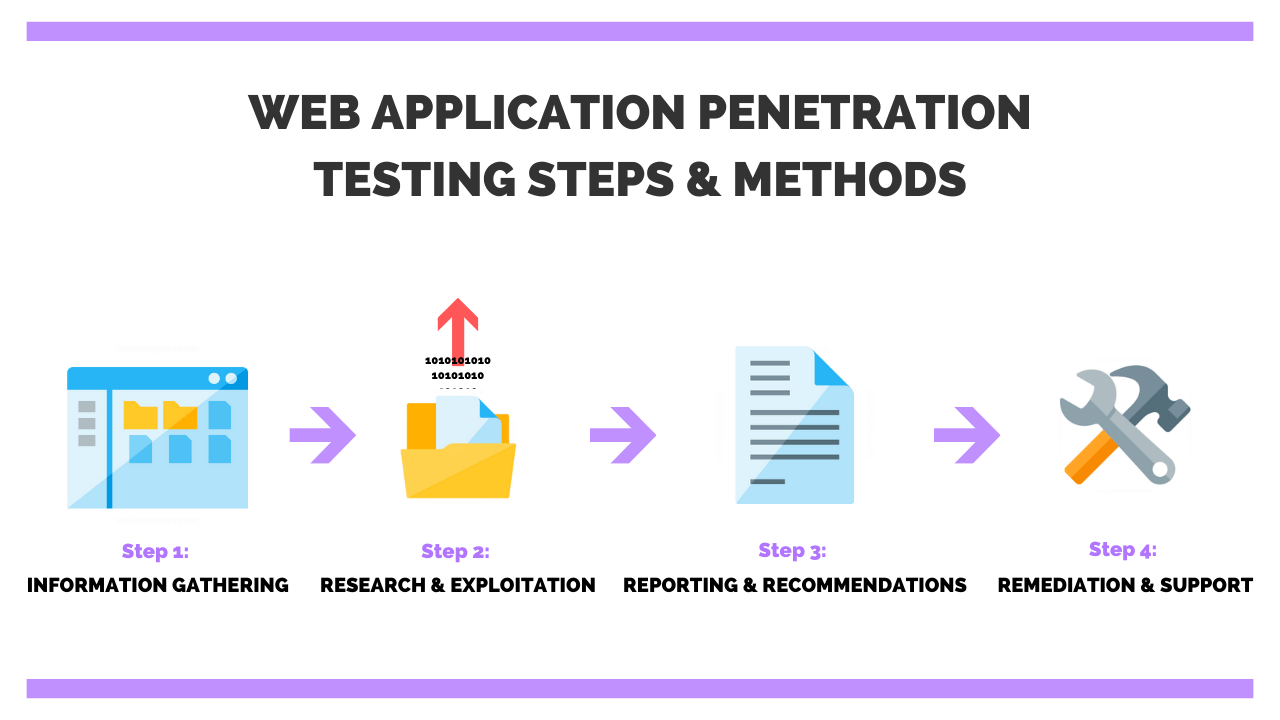






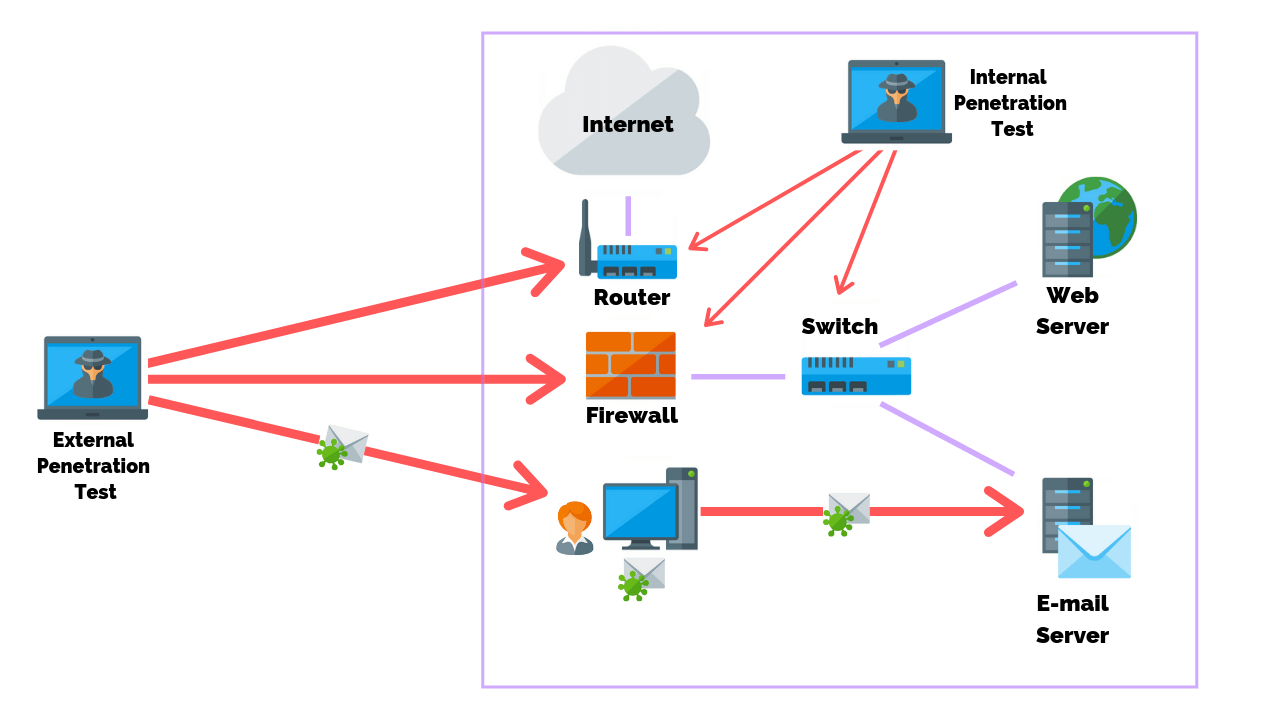
![Penetration Testing Report by Astra Security [Download] Penetration Testing Report by Astra Security [Download]](https://www.getastra.com/blog/wp-content/uploads/2021/07/Astra-Pentest-Dashboard-1-720x480.png)



![Breaking into Information… by Andy Gill [PDF/iPad/Kindle] Breaking into Information… by Andy Gill [PDF/iPad/Kindle]](https://d2sofvawe08yqg.cloudfront.net/ltr101-breaking-into-infosec/s_hero2x?1620533105)