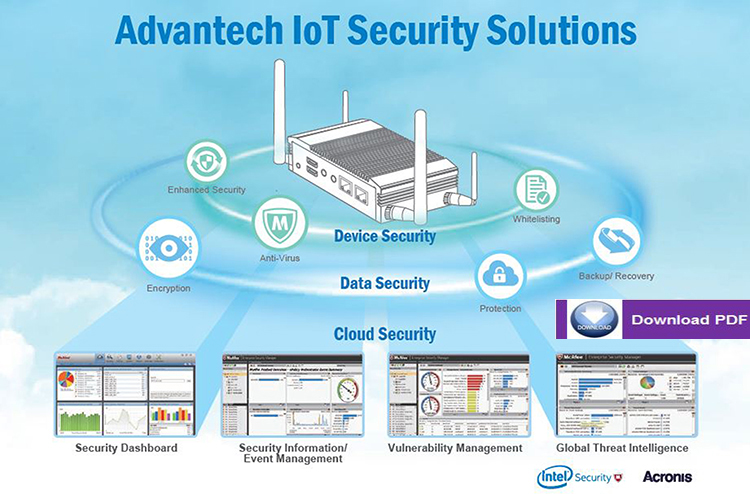
Amazon.com: GL-X750V2 (Spitz) T-Mobile/AT&T IoT Device Certified, 4G LTE VPN Router Without BLE Module, AC750 Dual-Band Wi-Fi, RV & Offshore Internet, OpenWrt, IoT Gateway, MicroSD Cardslot, North America only : Electronics
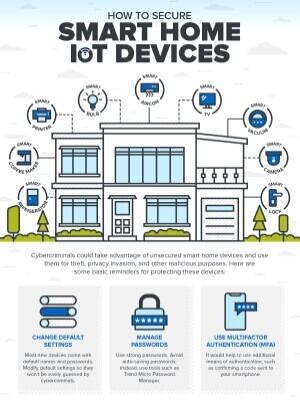
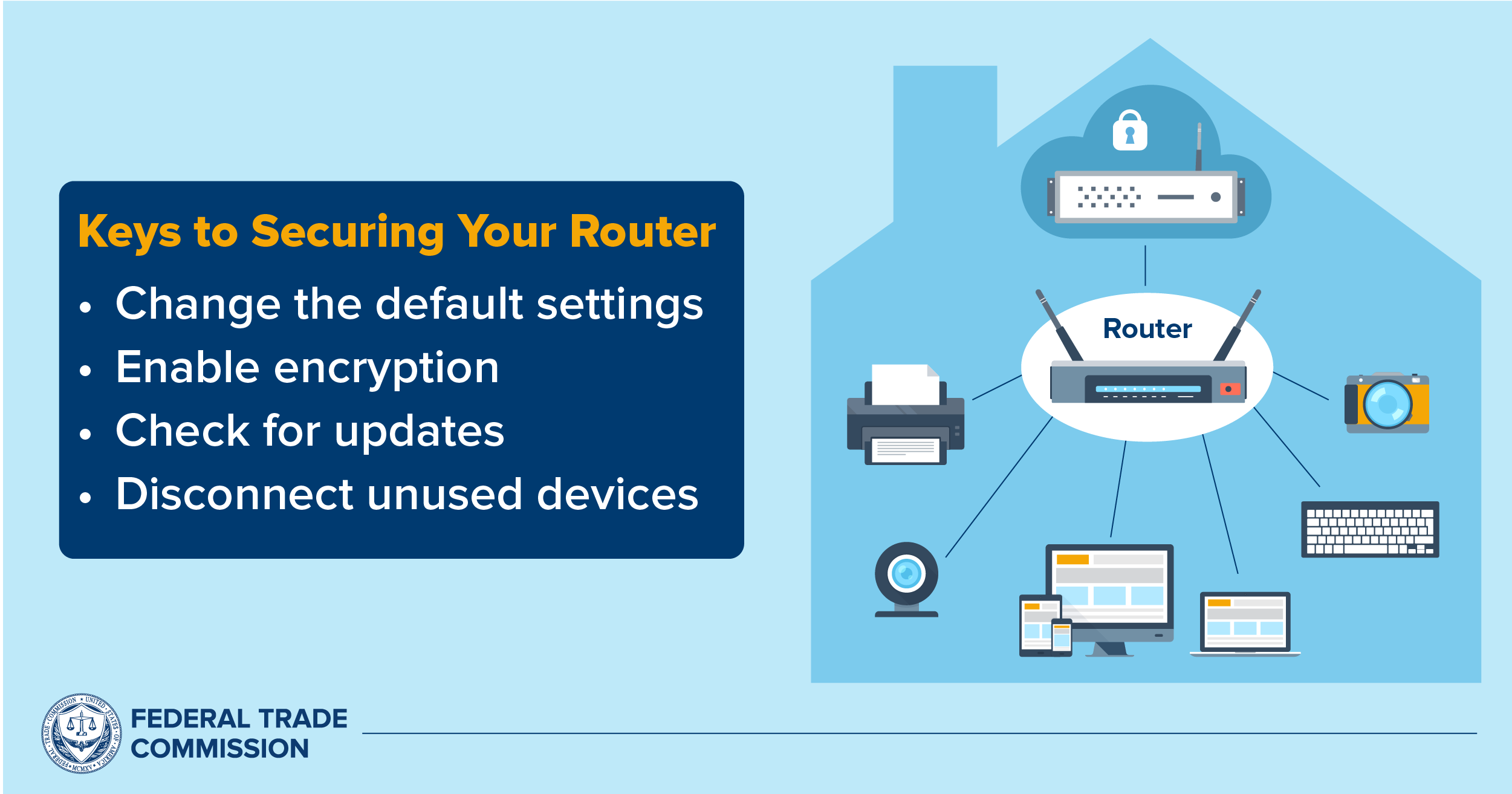
How to Secure Smart Home IoT Devices, Routers, and Smart Speakers - Nouvelles de sécurité - Trend Micro FR