USB HID keyboard: why 4 URBs are generated for a keypress instead of 2? - Electrical Engineering Stack Exchange
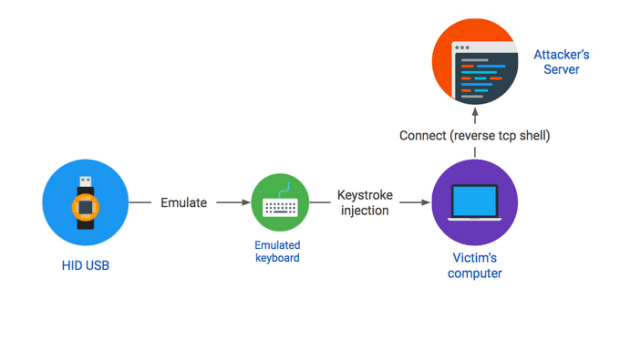
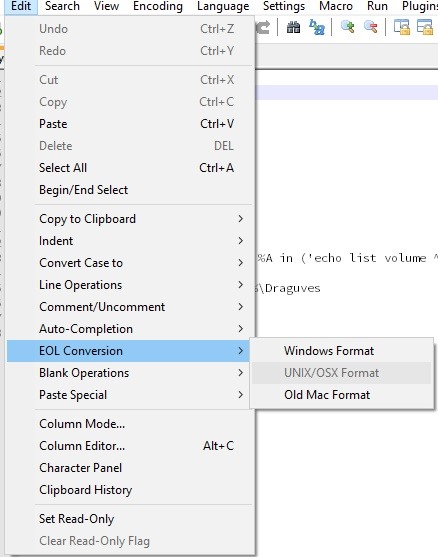
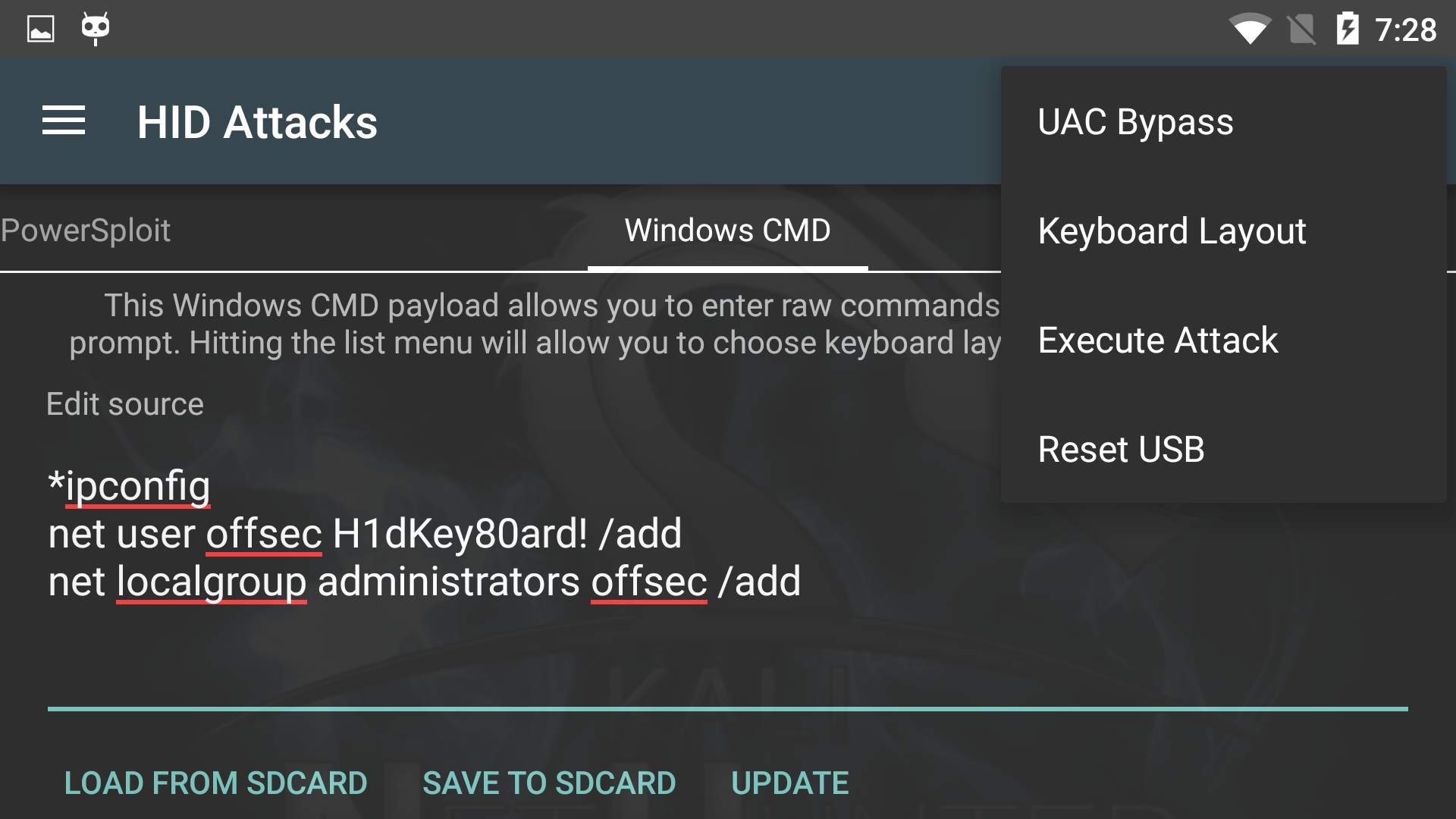
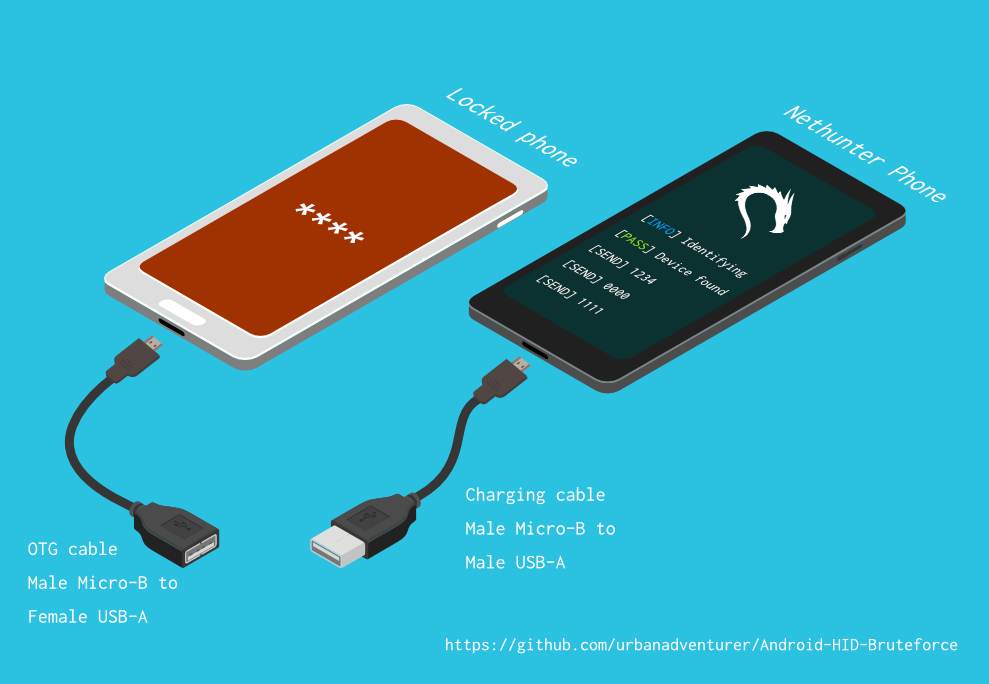
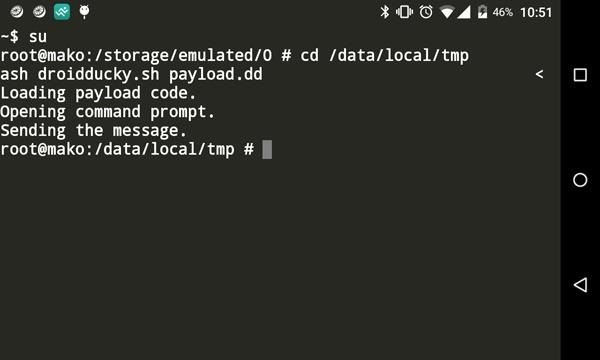
Nexus 10] HID Attack / Keyboard not working · Issue #125 · offensive-security/kali-nethunter · GitHub

Darren Kitchen on Twitter: "Here's something crazy ⌨️💡🪞 — Stealing data OVER CAPSLOCK! Did you know keyboard LEDs are bi-directional? Keystroke Reflection is a new side-channel exfiltration attack for the NEW 🐤