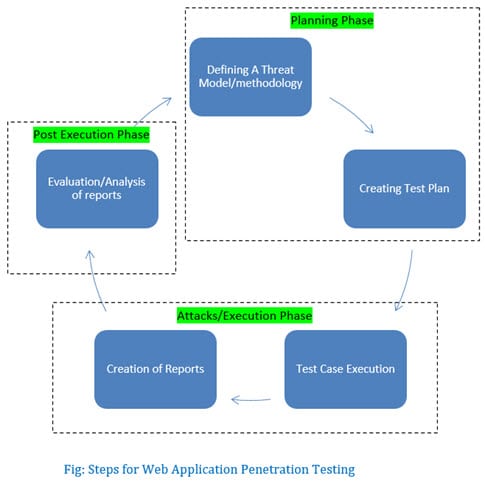
Shubham Sharma on Twitter: "Web App Penetration Testing Credit: https://t.co/Tk48DQLqct #infosec #cybersecurity #pentesting #oscp #informationsecurity #hacking #DataSecurity #CyberSec #Hackers #tools #bugbountytips #Linux #websecurity #Network ...

Web Server Penetration Testing Ppt PowerPoint Presentation File Graphic Images Cpb - PowerPoint Templates